Mobile applications have become essential for organizations across various industries, helping them to enhance their operations, engage with customers, streamline processes and boost overall productivity. They play a crucial role in end users daily lives by providing convenience, availability, facilitating communication, entertainment, and education. With this rapid evolution, ensuring the security of your Android apps is paramount. One of the most effective ways to achieve this is through Vulnerability Assessment and Penetration Testing (VAPT), which helps to identify and mitigate security vulnerabilities.
In this blog we explore VAPT and the process of conducting Static Analysis for Android applications using the in-house tool, DivyaAstra, developed by the SourceFuse Security Team as part of our VAPT efforts.
What is VAPT?
VAPT is a comprehensive security testing approach that aims to identify and address potential cybersecurity vulnerabilities in a system or network. Vulnerability Assessment involves scanning and analyzing a system to identify weaknesses or flaws that could be exploited by attackers. This might include outdated software, misconfigurations, or known vulnerabilities. Penetration Testing goes a step further by simulating an actual attack to assess the system’s resilience. This involves attempting to exploit identified vulnerabilities to gain unauthorized access or control.
There are four phases in VAPT of mobile applications, including Android and iOS:
- Static Analysis
- Dynamic Analysis
- Exploitation
- Reporting
Static Analysis testing plays a critical role in ensuring that the mobile application is bug-free, performs well and meets security standards. It is a crucial phase i.e. a method of debugging that involves examining the code without executing it. It is increasingly important today that mobile applications be secure, as an insecure application which is not configured and tested properly as per security standards can lead to numerous security issues such as data breaches, security misconfiguration issues, authentication/authorization issues.
There are many examples of actual security issues due to the failure of implementing data storage practices, such as encryption or secure containers. In one recent example, a vulnerability was discovered in PayPal’s mobile app, which stored user credentials in plaintext or improperly encrypted formats within the device’s local storage. This meant several Android banking apps failed to adhere to secure data storage guidelines recommended by Open Worldwide Application Security Project (OWASP) for storing sensitive data; this included usernames, passwords, session tokens, internal IP addresses, URLs, and infrastructure configuration.
Static Analysis Vulnerabilities Found by DivyaAstra
DivyaAstra, SourceFuse’s in-house tool, is a collection of open-source tools that collects critical information, including sensitive strings such as hard-coded data, IDs, API keys, passwords, tokens, IP addresses, private keys, secret keys, and bucket details. In addition to gathering sensitive data, the tool thoroughly evaluates the application ecosystem, including popular frameworks such as React and Flutter.
It performs reverse engineering to gain insights into application behavior and extracts vital information such as endpoints, Firebase data, and URLs. The script also analyzes Android XML files, which provide details on exported activities, services, receivers, and permissions, ensuring a comprehensive assessment of the application’s structure. Moreover, this tool leverages Nuclei template-based scans to perform crucial checks, including certificate validations, backup and debug configurations, and biometric detection. It identifies vulnerabilities in third-party libraries and flags any outdated software versions, thereby enhancing the security posture of the application.
This tool not only enhances the VAPT process but also fosters a proactive approach to mobile application security, making it an invaluable asset for developers and security professionals alike. It provides organized results, enabling team members to easily access and quickly understand the findings. The built-in automation capabilities also streamline the entire process, resulting in improved effectiveness and efficiency in VAPT activities. Overall, this tool enhances both teamwork and productivity in security assessments.
Key Elements of DivyaAstra
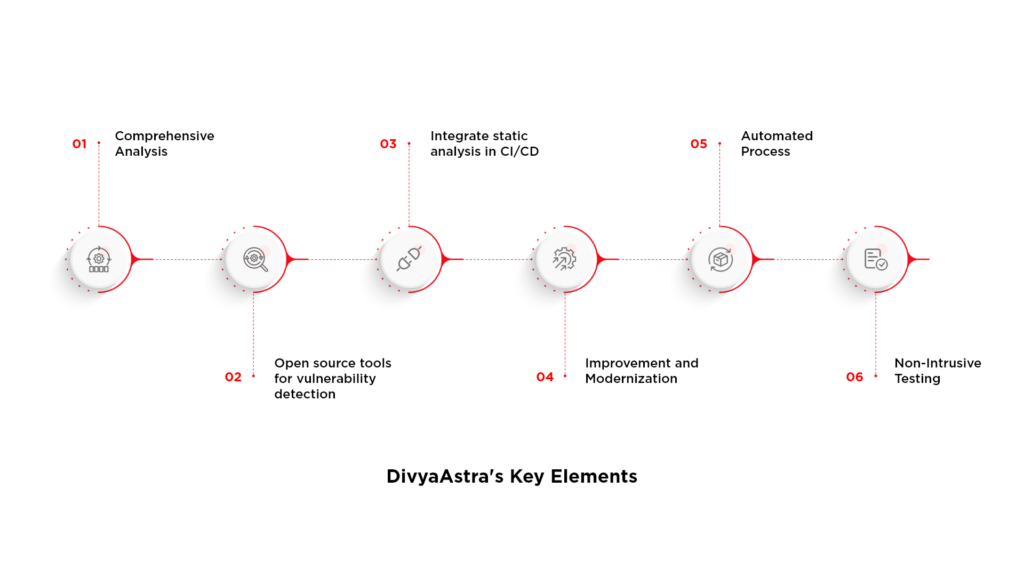
Comprehensive Analysis
The tool navigates through the static analysis phase of the mobile application, specifically for Android, and examines the entire Android APK file in the application to identify vulnerabilities.
Open-Source Tools for Vulnerability Detection
Tool identifies Sensitive Strings – Hardcoded data, IDs, API keys, Passwords, Tokens, IP Addresses, Private keys, Secret keys, and Bucket information, Code Obfuscation for Android – Reverse Engineering, Android XML File information and permissions such as Exported activities, services and receivers Etc.
Integrate DivyaAstra in CI/CD
Integrating this tool into the Jenkins CI/CD pipeline has been crucial in addressing security challenges in the software development lifecycle and aligning security practices with modern software delivery processes. This promotes a proactive approach to cybersecurity, allowing us to address current concerns and establish a forward-thinking security strategy that enhances our applications resilience against evolving threats.
Improvement and Modernization
On regular Intervals all the static analysis tools integrated in the script are upgraded once the latest version of the tool is available in the industry market.
Automated Process
Tools integrated into the script for static analysis can automate the scanning process, making it efficient and consistent.

Non-Intrusive Testing
Since, static analysis does not require the code to be executed, it is non-intrusive and does not interfere with the running application. This makes it safe to use in environments where running the code might not be feasible or could be risky.
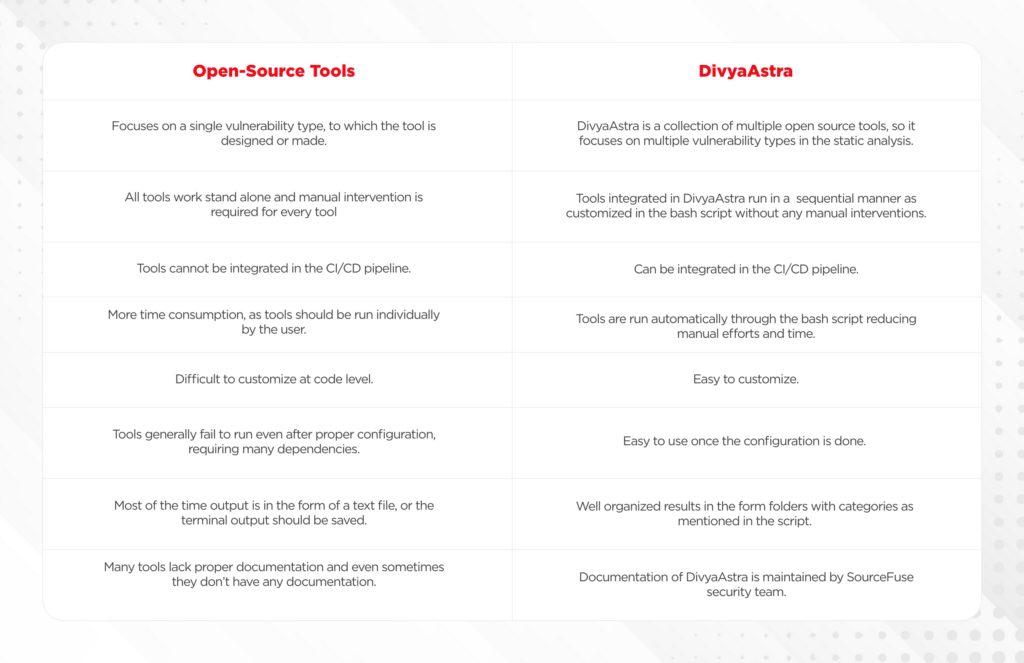
Open-Source Tools vs DivyaAstra

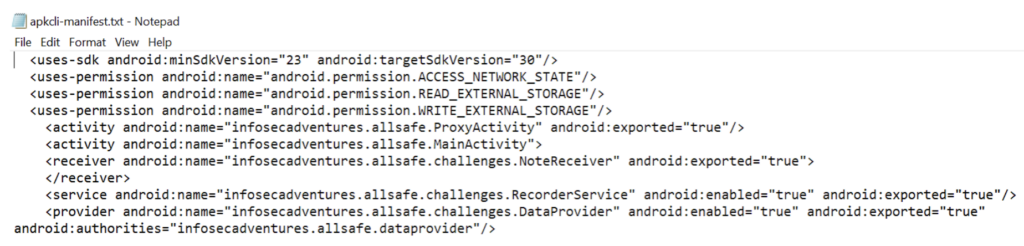
Steps to run DivyaAstra tool on the local host:
- Open Kali Linux/Ubuntu terminal and open the directory where the bash script is saved and run the tool by providing the complete path of the APK file.
Example: ./DivyaAstra.sh /users/carlos/test.apk - The script runs and the tools integrated in the script will run one by one, this can be observed in the terminal.
- Once the script is run successfully and it generates a zip file for the APK, once you extract it you can output files in the organized folders.
Example: Android – Bugs, Recon, Reverse, Urls - All the text files should be further reviewed for vulnerabilities identified by the script.
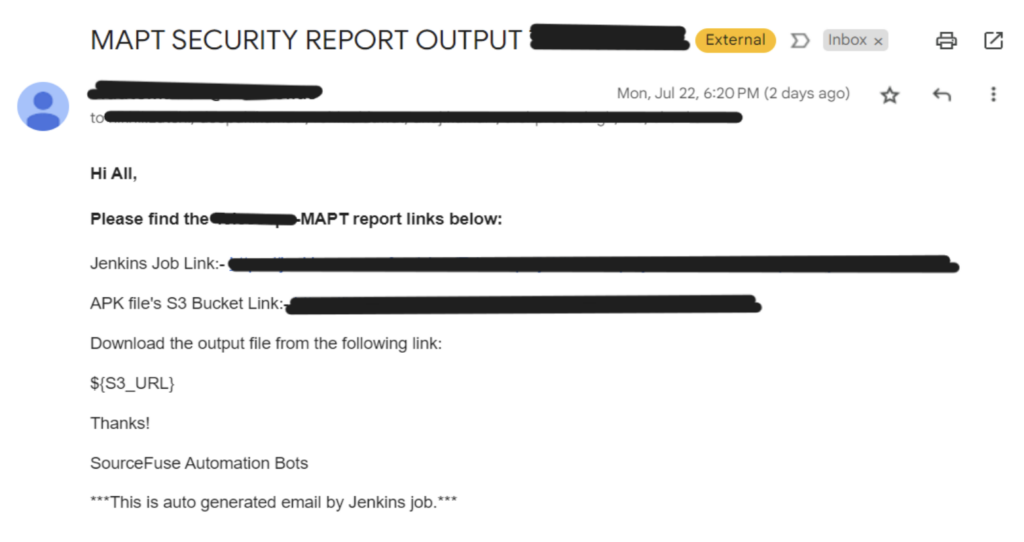
- To integrate DivyaAstra into Jenkins, first we need to install all the dependencies in the AWS instance(Ubuntu) and configure the Jenkins accordingly, then we need to run the build and once the build is successful the output attachment is sent to the mail.
DivyaAstra Coverage:
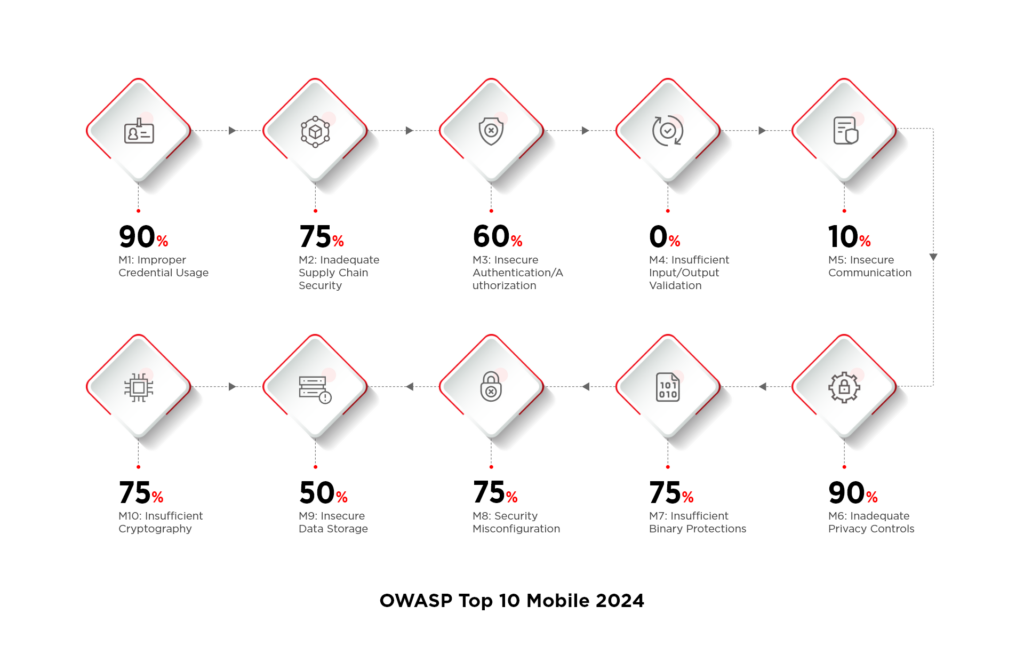
Benefits of DivyaAstra
- Improved Code Quality:
DivyaAstra enforces coding standards and best practices, ensuring that the code and configuration made for the mobile application is efficient and follows the defined guidelines by OWASP for Mobile.
- Increased Developer Productivity:
By automating the detection of common issues using this tool, it allows developers to focus on more complex and critical tasks, enhancing their productivity and reducing the time spent on debugging, helps in mitigating risks associated with software development and deployment.
- Early Vulnerability Detection:
DivyaAstra identifies potential vulnerabilities early, leading to fewer runtime errors and more stable software.
- Time and Effort Saving:
Automated scans with the CI/CD saves significant time and effort compared to manual review processes.
- Documentation and Maintenance:
Output from DivyaAstra is documented, continuously monitored and tracked on a timely basis and maintained by the security team for the references.
Conclusion
Static analysis in mobile security testing is a vital component of the VAPT process. By integrating this tool into your development process, DivyaAstra can identify and mitigate security vulnerabilities early in the development phase, reducing the time and efforts of the manual VAPT, ensuring that your app is robust and secure. Utilizing the right tools and following best practices will help you streamline the process and achieve better security outcomes.
Using DivyaAstra we have advanced the level of mobile application security testing in SourceFuse. If you’re interested in learning more about security testing, DivyaAstra, or other related topics, we invite you to connect with the knowledgeable professionals at SourceFuse. Our team is ready to provide insights and support tailored to your needs.